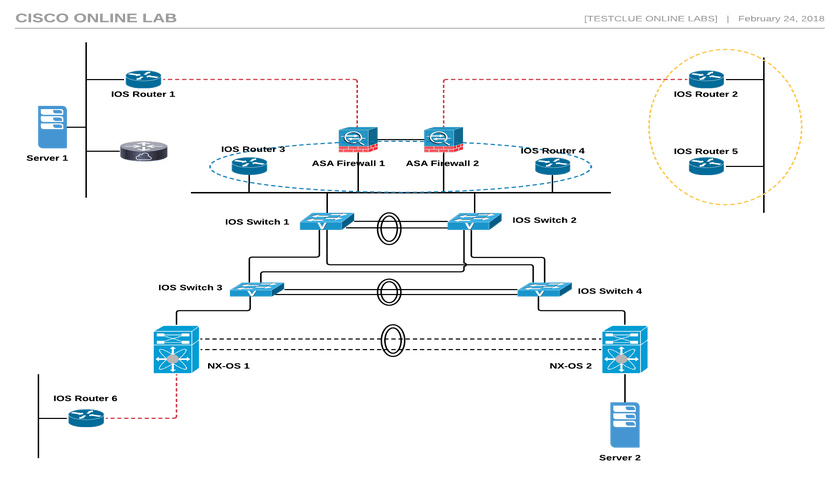
The Cisco Online Lab consists of 17 virtual appliances, including NX-OS, ASA FW, Cisco routers, and switches. It also includes two small servers for testing end-to-end configurations and topologies. On this page, you can find useful information about lab equipment, links, useful tutorials, and troubleshooting information. The network is based on VIRL and is built on a machine that provides 8 vCPUs, 21 GB RAM and 200 GB HDD storage.
Cisco Online Lab Setup
There may be a total of 17 nodes in different configurations (see the device list section below)
You can choose to use an existing topology or design your own exercise.
Once configured, local devices can be accessed via SSH / Putty.
Access the browser-based console session to configure the device.
The ready topology is shown on this page and can also be downloaded.
LAN server:
Two ubuntu servers are also provided in the topology
These are ubuntu machines that can be used for end-to-end testing of the network.
Find the server's IP address by running the "ifconfig" command from the console
Device List:
6x Cisco IOSv Router
4x Cisco IOSvL2 Switch
2x Mode Cisco ASA Firewall
2 NX-OS devices
2x Ubuntu Application Test Server
1 Windows 7 PC to configure
Internal network: DATA network 10.1.1.0/24
Laboratory information and instructions:
If you have already booked your server time, log in to the lab console below and email your credentials during the booking process. To book a new time, click here.
Log in to email user/pass via link above
Level 2 certification, will be emailed
List of Devices Available for Connection - Windows PC, Cisco Devices
Connect from listed connection to Windows 7 PC, with - labuser/Labroot12! @
Cisco Device Login - Cisco/Cisco
The laboratory will automatically destroy after 10 minutes from the end of the meeting
All lab devices are accessible via browser-based console/CLI access
To enable SSH to access the device from the Internet, add a default route to 192.168.80.1
Device IP Addressing and SSH Port (Available after adding a default route from the CLI console access)
Public IP SSH Access Port Cisco Device IP Device Type
No 192.168.80.221 2001 77.93.215.14
77.93.215.14 2002 192.168.80.222 LXC
77.93.215.14 2003 192.168.80.223 ASA 1
77.93.215.14 2004 192.168.80.224 ASA 2
77.93.215.14 2005 192.168.80.225 CSR
77.93.215.14 2006 192.168.80.226 Router 1
77.93.215.14 2007 192.168.80.227 Router 2
77.93.215.14 2008 192.168.80.228 Router 3
77.93.215.14 2009 192.168.80.229 Router 4
77.93.215.14 2010 192.168.80.230 Router 5
77.93.215.14 2011 192.168.80.231 Router 6
77.93.215.14 2012 192.168.80.232 Switch 1
77.93.215.14 2013 192.168.80.233 Switch 2
77.93.215.14 2014 192.168.80.234 Switch 3
77.93.215.14 2015 192.168.80.235 Switch 4
77.93.215.14 2016 192.168.80.236 NX-OS 1
77.93.215.14 2017 192.168.80.237 NX-OS 2
No NA 192.168.80.238 Ubuntu 1
No NA 192.168.80.239 Ubuntu 2
Useful links:
Cisco ASA Firewall Configuration Guides
Cisco ASA Firewall Configuration using CLI 8.2
Cisco NX-OS Configuration Guide
For troubleshooting and technical discussions, use this forum:
Questions during the experiment class
Have problems during the lab meeting? Please email support@testclue.com and we will respond to your question within 10 minutes. Frequently asked questions can also be discussed and supported through the forum. Loss of connectivity, loss of connectivity to the lab portal, topology changes, etc. can be sent directly to master@testclue.com
